September 16, 2024 – Oracle WebLogic Server, a key platform for developing and managing enterprise applications, has become the latest target of a new Linux malware named “Hadooken.” This malware, discovered by Aqua Nautilus researchers, is exploiting weak admin credentials to infiltrate systems.
Malware Details
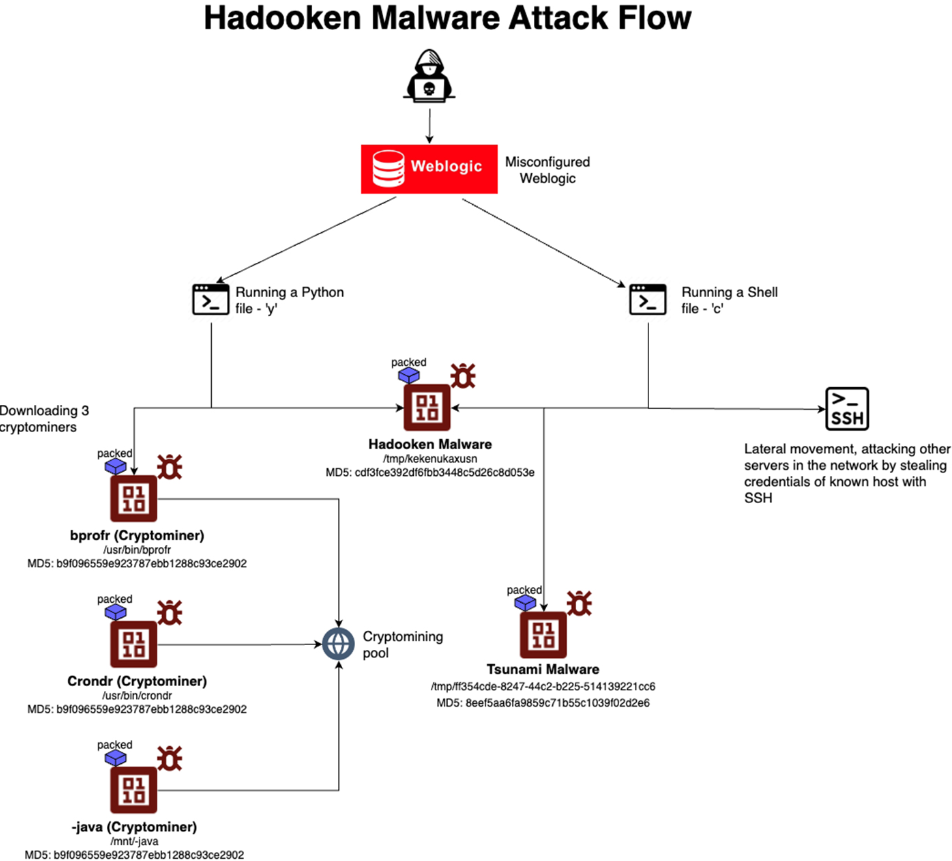
Hadooken malware is designed to exploit Oracle WebLogic servers by leveraging weak admin credentials. Once it gains access, it deploys two primary components:
- Cryptominer: (MD5: 9bea7389b633c331e706995ed4b3999c)
- Tsunami Malware: (MD5: 8eef5aa6fa9859c71b55c1039f02d2e6)
The attack uses shell and Python scripts to download and execute payloads, targeting non-persistent directories like /tmp.
Deployment and Persistence
The cryptominer is installed as ‘/usr/bin/crondr’, ‘/usr/bin/bprofr’, and ‘/mnt/-java’, while Tsunami malware uses a random filename in /tmp. Persistence is maintained through cron jobs created in /etc/cron.<Period>/<Random String> with varying frequencies.
Lateral Movement and Evasion
Hadooken searches for SSH data in various directories and employs evasion techniques such as base64 encoding, log clearance, and process masquerading.
Associated IP Addresses and Ransomware Links
The malware is linked to IP addresses 89.185.85.102 and 185.174.136.204, which are associated with potential ransomware distribution, including Mallox (MD5: 4a12098c3799ce17d6d59df86ed1a5b6), RHOMBUS, and NoEscape. A related PowerShell script ‘b.ps1’ (MD5: c1897ea9457343bd8e73f98a1d85a38f) is used to distribute Mallox ransomware, indicating a multi-platform attack strategy.
Vulnerability Exposure
Shodan reveals over 230,000 internet-connected WebLogic servers, with several hundred exposed admin consoles vulnerable to exploitation.
Mitigation Strategies
To protect against such threats, experts recommend the following measures:
- Use IaC scanning tools to detect misconfigurations before deployment.
- Employ CSPM tools to scan cloud configurations for risks.
- Scan Kubernetes clusters for misconfigurations.
- Secure container images and Docker files.
- Monitor runtime environments.
Conclusion
The discovery of Hadooken malware underscores the critical need for robust security measures for Oracle WebLogic servers. Organizations are urged to implement the recommended mitigation strategies to safeguard their systems from such sophisticated attacks.
Join Our WhatsApp Channel for daily updates and free resources: Click Here