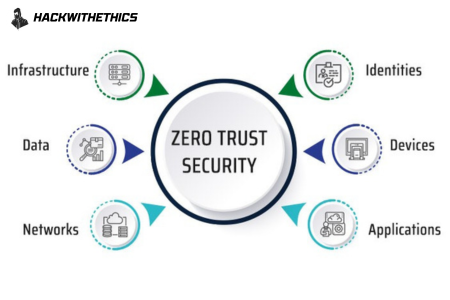
Zero Trust Architecture (ZTA) Demystified: Charting The Future Of Cybersecurity
In an era where digital landscapes are evolving at an unprecedented pace, traditional cybersecurity models are being put to the test. The rise in sophisticated cyber threats has led security experts to reevaluate their strategies. One paradigm that has gained significant attention is the Zero Trust Architecture (ZTA). In this blog post, we’ll delve into…










