September 24, 2024 – In a concerning development for the cybersecurity community, researchers have uncovered a new malware strain named PondRAT, which is being distributed through compromised Python packages. This sophisticated attack, attributed to North Korean threat actors, specifically targets software developers and poses significant risks to the software supply chain.
The Discovery
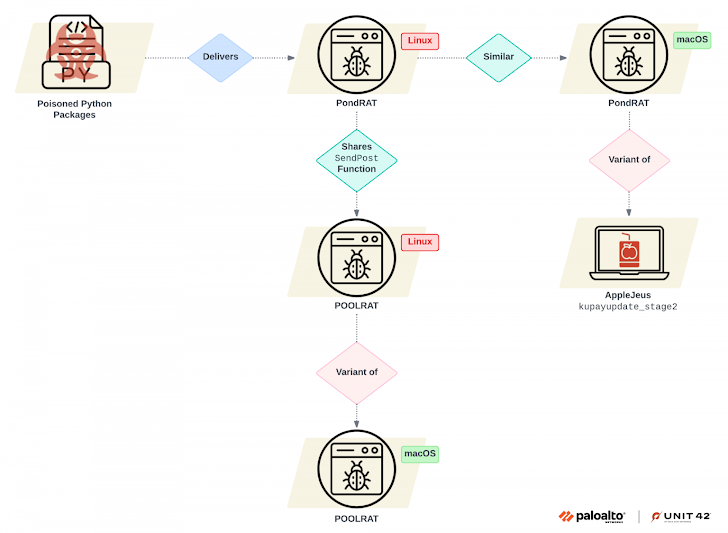
The malicious campaign was identified by researchers from Palo Alto Networks Unit 42. The attackers, linked to the notorious Lazarus Group, have been using the Python Package Index (PyPI) to upload poisoned packages. These packages, disguised as legitimate open-source projects, have been downloaded hundreds of times before being detected and removed12.
Technical Details
PondRAT is a Remote Access Trojan (RAT) that allows attackers to gain unauthorized access to infected systems. It is a lighter version of the previously known POOLRAT malware, designed to target both Linux and macOS platforms. The malware is capable of uploading and downloading files, executing arbitrary commands, and pausing operations based on preconfigured intervals12.
The compromised packages identified include:
- real-ids (893 downloads)
- coloredtxt (381 downloads)
- beautifultext (736 downloads)
- minisound (416 downloads)12
Impact and Mitigation
The primary targets of this campaign are individual developers and supply chain vendors. By compromising these entities, the attackers aim to infiltrate larger networks and potentially cause widespread damage. The impact of such an attack can be severe, leading to data exfiltration, network infiltration, and significant operational disruptions12.
To mitigate the risks, organizations are advised to:
- Monitor for unexpected network connections from developer systems.
- Implement behavioral analysis to detect unusual Python package installations.
- Use file integrity monitoring on critical system and application files.
- Deploy endpoint detection and response (EDR) solutions to identify suspicious activities12.
Conclusion
The discovery of PondRAT highlights the evolving tactics of cybercriminals and the importance of robust cybersecurity measures. Developers and organizations must remain vigilant and adopt proactive strategies to safeguard their systems against such sophisticated threats.
For more detailed information and updates on this ongoing investigation, stay tuned to our cybersecurity news section.